The Zyxel USG Flex 100 is the entry-level security firewall gateway from the new USG Flex series and yes, it does have pretty much all the features of the older USG series, but Zyxel now relies a lot more on the Cloud Query service (that it has unveiled last year) to help deliver a better UTM firewall performance, while requiring less resources from the device itself. This way, there is a far higher detection rate for possible threats (while in the past it would have gone beyond the hardware capacity).
| Zyxel USG Flex 100 | |
|---|---|
| Zyxel.com | Check Product |
Of course, the internal hardware has been improved (to meet the exigence of 2020) and yes, the SSL, IPsec and L2TP-based VPNs are still there (as well as the large amount of customization), but why call it FLEX?
It’s an acronym for Flexible and it refers to the subscription plans which are more flexible: the user can either choose single license configurations or migrate unexpired ones from older USG devices.
Besides the Zyxel USG Flex 100, the manufacturer has also made available the Flex 200 and Flex 500 which are a bit more faster and have a higher variety of ports – while the rest of the devices from the series have more than one WAN port, the Flex 100 seems to be the only member to come with a single WAN port (it does have an SFP port and support for 3G/4G modems, as well as the OPT port, all with the potential of functioning as an additional WAN interface).
IMPORTANT: It was found that the USG series running the ZLD v4.60 is vulnerable to third-party attacks (a backdoor account was discovered), so you should immediately update the device to get the latest patch that fixes this vulnerability.
Update: The Zyxel USG Flex 100 can now be used with the Nebula Cloud management and you can check a more in-depth analysis here.
Design and Build Quality
If you’re familiar with Zyxel USG40 (or the newer NSG50), the USG Flex 100 has pretty much the same design and it’s no surprise since the USG Flex 100 is also known as USG40v2. The gateway features a metallic gray box with a plastic front and with a couple of red accents on the left and right side which are characteristic to the series. Furthermore, the device is very compact (it measures 11.18 x 7.48 x 3.94 inches) and no, you won’t be able to mount it in a rack since there are no holes on the sides to allow you to attach any extensions (if you must put it in a rack, there is the tray option). Inside the package, there are four rubber feet which need to be glued to the bottom of the Flex 100 if you intend to leave it on a desk, otherwise, there are two dedicated holes on the bottom to mount the device on the wall.
Another similarity with the Zyxel USG20-VPN is that this gateway is fanless (the original USG20 did have a fan), so it fully relies on passive cooling. At the moment, there are about 86 degrees F outside (approx 80 inside) and I noticed that the Zyxel USG Flex 100 did get a bit warm on the top and hot on the bottom which means that those feet are mandatory to allow some airflow underneath the case; despite running a bit hot, there were no signs of throttling or overheating – it’s worth mentioning that Zyxel has added lots of cut-outs on the top of the device, as well as on the sides to keep the internal temperature low. In terms of power consumption, since this is the entry-level model, it is also the most efficient, requiring no more than 7 watts (on average) and at full load, it can go up to 12.5 W (which is still quite low for a networking device of its caliber).
On the front of the device, next to the red plastic piece with the name and number, there’s a recessed Reset button (press and hold it for about 5 seconds until the SYS LED starts blinking to return the device to its default settings), followed by two LEDs: PWR (if it gets red, then there’s a hardware failure) and SYS (flashes green when the gateway is booting). Further to the right, there are six LEDs, from P1 to P6 (WAN/LANN/DMZ) and these LEDs are going to be yellow when the connection is made at 1000Mbps or green, when the connection is made at 10/100 Mbps. Lastly, there’s a USB 3.0 port which can be useful for connecting external storage devices or 3G/4G USB modems (for WAN failover).
On the rear side of the Zyxel Flex 100, there is a 12V Power connector, an ON/Off button, a Gigabit SFP P1 port (suitable for a fiber connection), a Console port (this port can be used to manage the device via CLI commands – Zyxel has added a Console cable inside the package and be aware that the host computer does need to have a communication software configured in a certain way – check the official user guide at page 71), a WAN P2 port (for the main Internet connection) and four other LAN/DMZ ports (P3 to P6).
| Zyxel USG Flex 100 | Zyxel USG Flex 200 | Zyxel USG Flex 500 | |
| LAN Ports | 4 | 4 | 7 |
| WAN Ports | 1 | 2 | Configurable |
| SFP Ports | 1 | 1 | 1 |
| USB Ports | 1 | 2 | 2 |
| Console Ports | 1(RJ-45) | 1(DB9) | 1(DB9) |
| Firewall Throughput (Mbps) | 900 | 1,800 | 2,300 |
| VPN Throughput (Mbps) | 270 | 450 | 810 |
| IDP Throughput (Mbps) | 540 | 1,100 | 1,150 |
| Max. IPsec VPN tunnels | 40 | 100 | 300 |
| Max. SSL VPN users | 30 | 60 | 150 |
Hardware
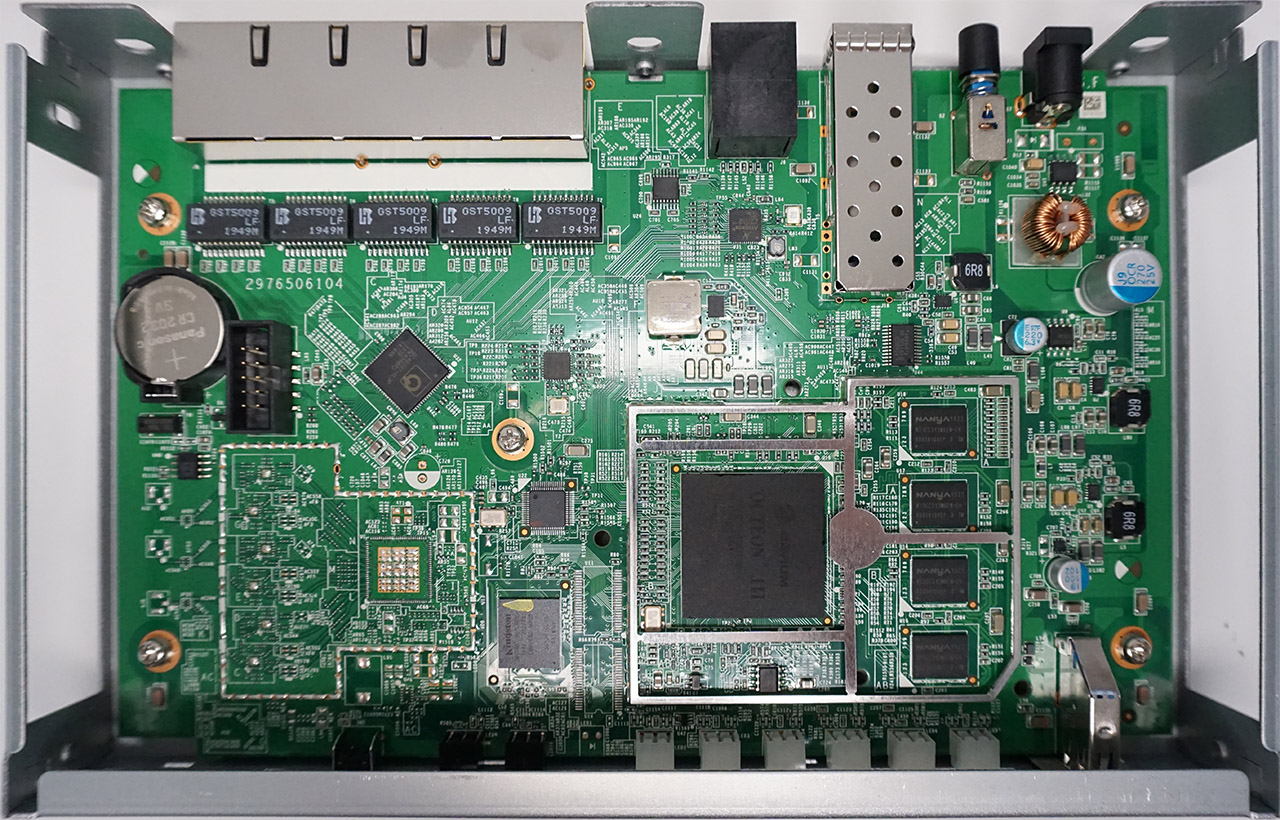
To have a look at the internal hardware of the Zyxel USG Flex 100, I removed all the six screws (be aware that there’s one hidden underneath the sticker with the Zyxel logo) and, after removing the small aluminum cover, I saw that Zyxel still favors Cavium, so the USG Flex 100 is equipped with a dual-core Cavium Octeon III CN7020-1200WG640-AAP-G chip (clocked at 1.2GHz) and four Nanya 1922 NT5CC512M8EN-EK (amounting to 2GB DDR3).
Furthermore, I could also identify a QCA8337 AL3C PK9398R3 Ethernet switch, a Qualcomm Atheros AR8033 AL1A NJ941229 PHY 3-CH 10Mbps/100Mbps/1Gbps, 8GB of flash memory from Kingston (EMMCC08G-M325), an Intel ALTERA 5M160ZE64C5N CPLD, a SIPEX 3232EC 1913L HCW8J transceiver, four GST5009 LF 1949M 1000 Base-T Magnetics Modules and a NXP PCA9555 24-pin CMOS device. As you can see, there are no WiFi chips or antennas and that’s because this firewall gateway doesn’t support WiFi.
The entire Flex series lacks a model with WiFi (some other USGs did come with external antennas – the models that would end with W) so, to connect your wireless clients, you will have to rely on some wireless access points.
As a side note, the Zyxel USG Flex 100 was designed to seamlessly integrate with some Unified and Unified Pro models, such as the NWA5123-AC HD. What you gain by sticking with Zyxel APs is central management, data forwarding, auto provisioning and yes, there’s also support for ZyMesh.
Zyxel USG Flex 100: Installation and Configuration
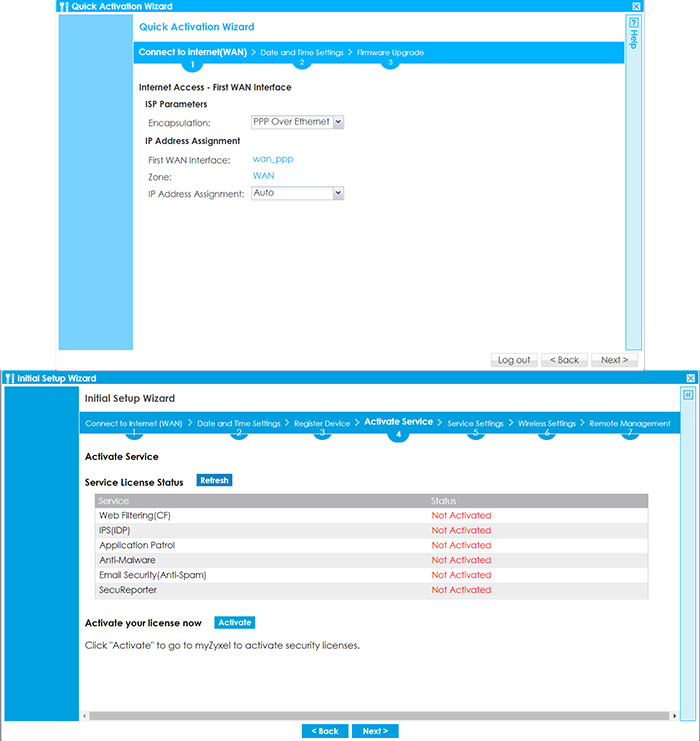
The installation process is very straight forward and it’s very similar to the one on consumer-grade routers: connect the WAN port to the modem, the Power cable and turn the device on and lastly, use an Ethernet cable to connect the firewall gateway to a computer; you can also add any wireless access point since the wizard will allow you to make a quick WiFi configuration. After the USG Flex 100 is connected to a computer, enter 192.168.1.1 in the browser and insert admin/1234 for the username and password. You will then be prompted to change the password and you can start the Quick Activation Wizard. On the first step, you can configure the First WAN interface (this model does not have the Second WAN interface config available in the Wizard), which, in my case, it was PPPoE, followed by the Date and Time set up and the Firmware Upgrade.
From here on, you can register the device and, if you already have an account, it’s going to be a matter of two clicks and you don’t have to enter any data since the process is automatic. After the product has been registered, you will arrive at the Activate Service window; here, there are the available Service License Status where there’s the option to quickly activate your license (again, with only a couple of clicks). If you decide to do it later, it can be easily done by visiting http://portal.myzyxel.com, entering your credentials and then manage your registered devices, the licenses and there’s also the option to download the latest firmware. Returning to the Wizard, the next page is the Service Settings, where you can Enable or Disable various services (such as URL Threat Filter, the Anti-Malware, IDP, Content Filter, App Patrol, Email Security and SecuReporter). You can also quickly set up the Wireless Settings (if you have a wireless access point available) and enable the Remote Management.
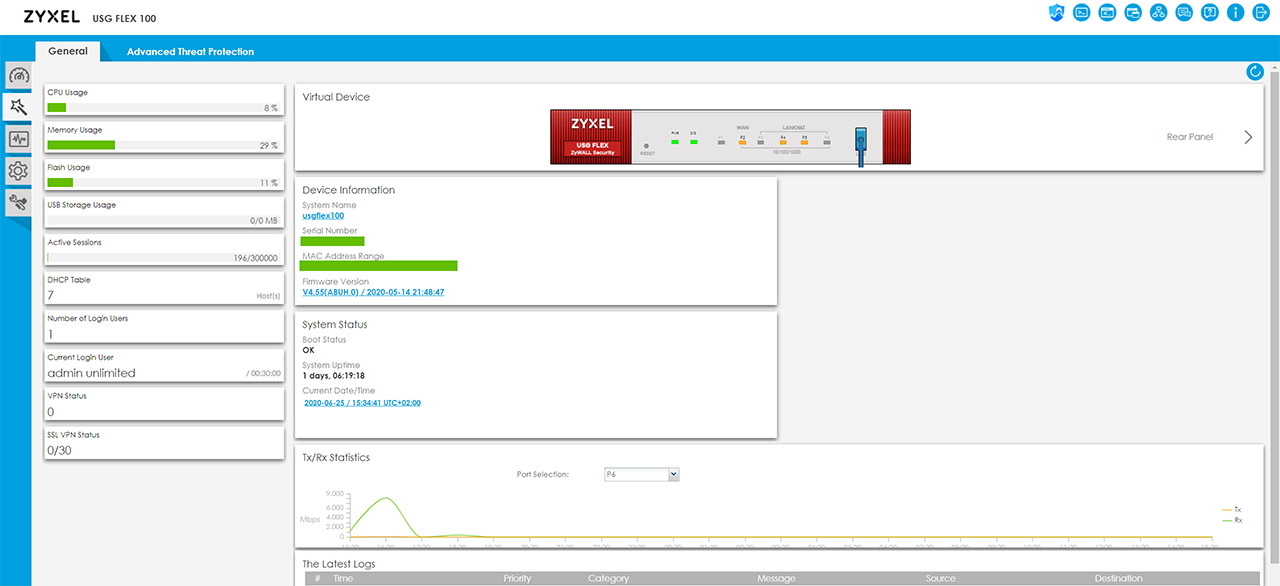
After that’s done, you can now roam the interface and there are a few elements that immediately stand out. The first one is the Virtual Device section, where you get to see an accurate graphical representation of both the front and the rear side of the device, then, there are various boxes containing different sets of status info, such as the Device Information (you can also update the firmware here), the System Status, CPU, Memory and Flash Usage and more.
Next to the General section, there’s also the Advanced Threat Protection section, where you get to see the security features in action (the number of scanned files, the number of threats found and more). Before moving on, it’s worth mentioning that on the top right side, there is an area where you can visit the SecuReporter (it’s a completely separate interface on the Zyxel servers). There’s also the possibility to use the Web Console and CLI, to check the Site Map and Logout.
Dual-WAN and Load Balancing
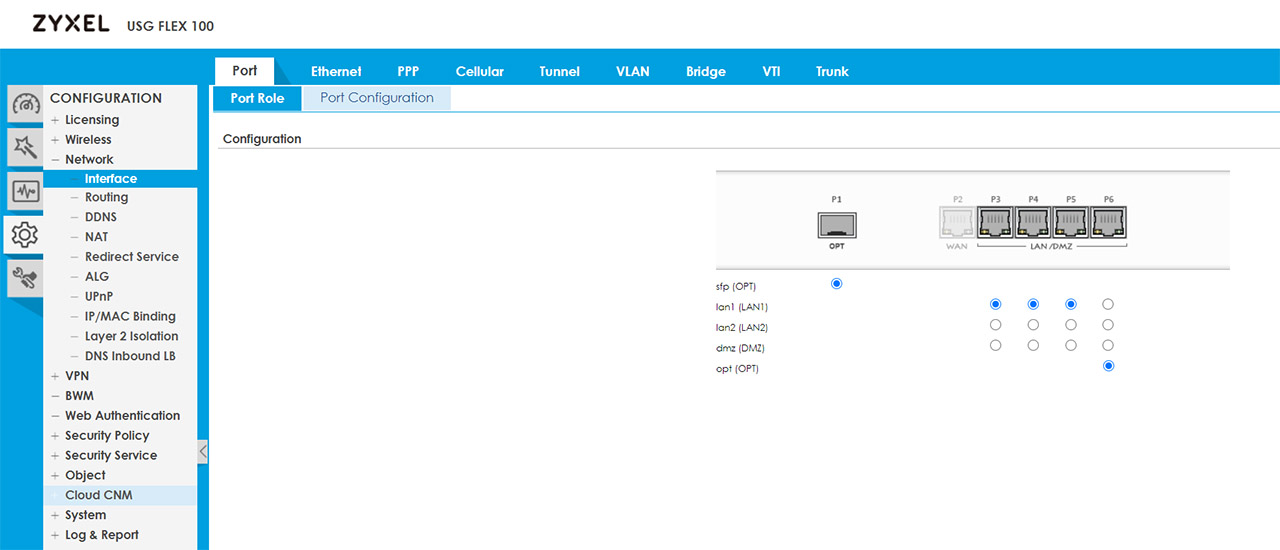
The Zyxel USG Flex 100 has a single default WAN port (that you can configure in the Wizard), but you can also set up a secondary Internet connection by clicking on the Quick Setup, selecting the WAN Interface and then choosing between the three available options: SFP, WAN or OPT. For this application, I selected the OPT port and since I had a secondary PPPoE connection that I borrowed from a neighbor, the setup process is going to be similar to the first WAN connection. To view the Ports and do any further adjustment, go to Configuration > Network > Interface.
If you have more than one ISP connection and want to balance the traffic load for a better bandwidth utilization, you will have to use trunks (Network > Interface > Trunk). Without doing any changes to the previous configuration and simply disconnecting any of the two links, I saw that the router would automatically switch to the active links and that’s because the USG Flex 100 uses the System Default WAN Trunk, which, in turn uses the Least Load First algorithm. This algorithm decides which interface should be used for the traffic by checking the outbound bandwidth utilization of each member interface (there is also the option to use the inbound traffic from the LAN or both the inbound and the outbound traffic).
Zyxel USG Flex 100
-Pros
- Supports IPSec, SSL and L2TP VPN
- Anti-Malware, ISP and other security related features
- The device is very compact
- Multi-WAN support + various load balancing algorithms
- Lots of walkthroughs and tutorials available
Cons
- It does get a bit hot on the bottom side
- A lot of features (such as the IPSec VPN client) are under license

Mark is a graduate in Computer Science, having gathered valuable experience over the years working in IT as a programmer. Mark is also the main tech writer for MBReviews.com, covering not only his passion, the networking devices, but also other cool electronic gadgets that you may find useful for your every day life.