The Zyxel Flex 100 and the entire USG Flex series have been well regarded as reliable security firewall solutions, but even though Zyxel has been actively developing its Cloud management platform, the USG series has been left out of the Cloud servers and, if you wanted a security-focused gateway, you had to rely on the NSG series. This includes the NSG50, a device that I tested a couple of years ago and it offered a myriad of security options (such as IDP, Anti-virus services, Content Filtering, Application Patrol and more), but it was essentially only Cloud-managed.
So, the possibility to integrate the USG Flex 100 into the Cloud platform bridges this gap between the ‘traditional’ management features and the Cloud-only-suitable abilities (such as the possibility to monitor a huge amount of devices and configure them by site). It’s worth mentioning that the FLEX series had its own well-established ecosystem and it doesn’t offer only a complete set of security options, the USG FLEX 100 could also manage wireless access points (although, it had no built-in PoE, so you had to rely on an additional Ethernet switch).
That being said, I have already had a look at the Zyxel USG Flex 100, so I’m not going to focus at all on the design or the internal hardware, nor will I go in-depth with the non-Cloud user interface. Instead, I’ll just check out how well the security gateway integrates within the Cloud management platform alongside the multi-Gigabit Ethernet switch XS1930-12HP and the WiFi 6 WAX650S.
License changes
Before that, I have to point out that Zyxel has made a significant change to the license system and the USG Flex integration with the NCC seems to have played an important part in this matter. The main change is that the license is now per-device instead of the co-termination type, where you essentially had a single expiration date for all licenses (so, if you added a new one, all other licenses would be re-calculated so they would all expire at the same time). If you already have a USG firewall and it has an active co-termination license, it will automatically be converted to per-device license (with the global organization expiry date set to the individual device). In case you have a key that’s not yet activated, you can exchange it for a per-device license.
Some of the changes that are specific to the USG Flex series are that Zyxel will add a few new security services, the UTM Security Pack on Nebula (includes UTM, Security Profile Synchronization, Analytics, Reporting and Response) and the Secure WiFi that adds support for a direct tunnel from a wireless access point to a remote USG Flex gateway.
How easy is it to add the Zyxel Flex 100 to the Nebula Control Center?
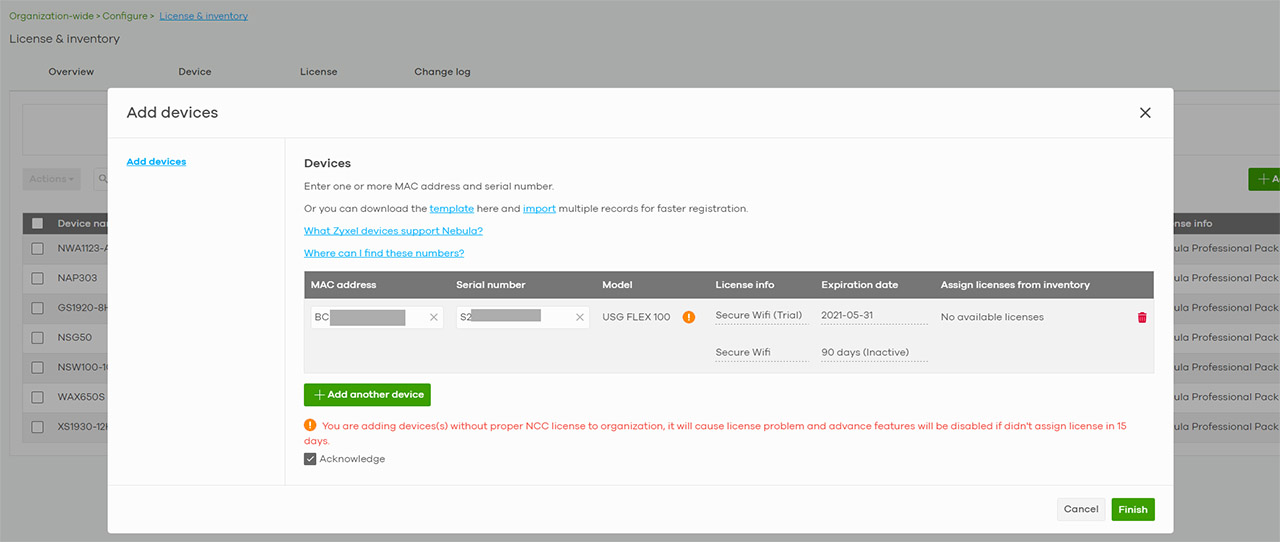
I know you think that it should be the same process as with other NCC-compatible Zyxel devices but it currently is a bit more complicated. The first step is to log into the Cloud management platform (or create a new account), then go to your Organization, create a new site or use an existing one and click on Organization-wide to visit the License & inventory section (yes, they have made some changes to the layout). Here, click on Device and you should see the Zyxel products that are already a part of the Cloud platform (if you have previously added any) and, by pressing on the Add button from the right side, you should be able to enter the Serial number and the MAC address (from the rear side of the NSW100-10P). The gateway will now be in the Inventory list and waiting to be added to a site. At this point, select the device and then from Actions, select Change site assignment to your current site.
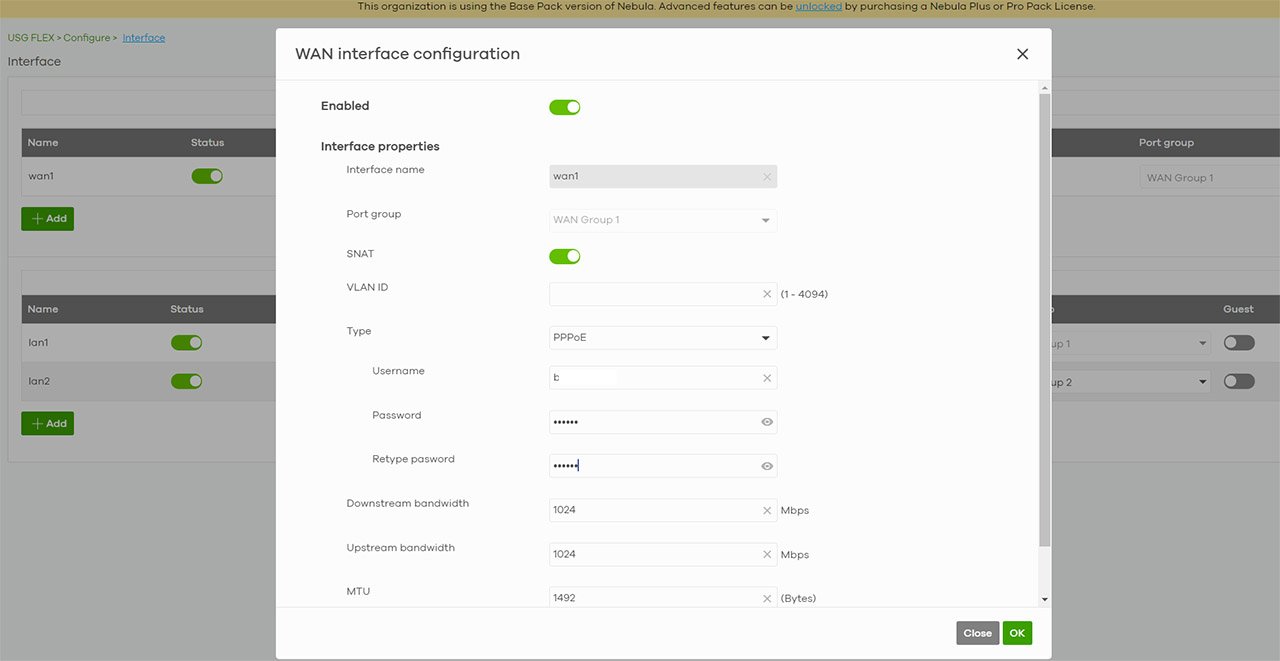
Be aware that you will not be able to add more than one security gateway to one site (either remove an existing gateway or create a new site). Before moving forward, it’s extremely important to have already set up the WAN connection, because otherwise the adoption process will fail. To do so, go to the USG FLEX option from the menu on the left, select the Interface and, at the WAN interface section, click Edit. This way, you can select the connection type (in my case, it was PPPoE) and, if required, to enter the ISP username and password.
The next step involves generating the ZTP config email (Zero Touch Provisioning) to significantly cut the configuration time (install it yourself or send it to a third-party email). After receiving the email, you should back-up your current configuration before moving to Nebula (Maintenance > File Manager > Configuration File) and then if you haven’t already, download and install the latest firmware version (follow these steps if you have already used the USG Flex 100 for a while). After that’s done, reset the gateway to the default factory settings (press and hold the Reset button for at least 5 seconds).
Wait until the SYS LED turns solid green (it can take a couple of minutes) and then click on the link provided in the email, the one that says Allow Nebula to Manage My Device. Now you only have to wait for the process to run its course and until the message appears saying that the pairing has been successful. Now, the Zyxel USG FLEX 100 should be a proper member of the Cloud managed gateway family.
The Software and the Features
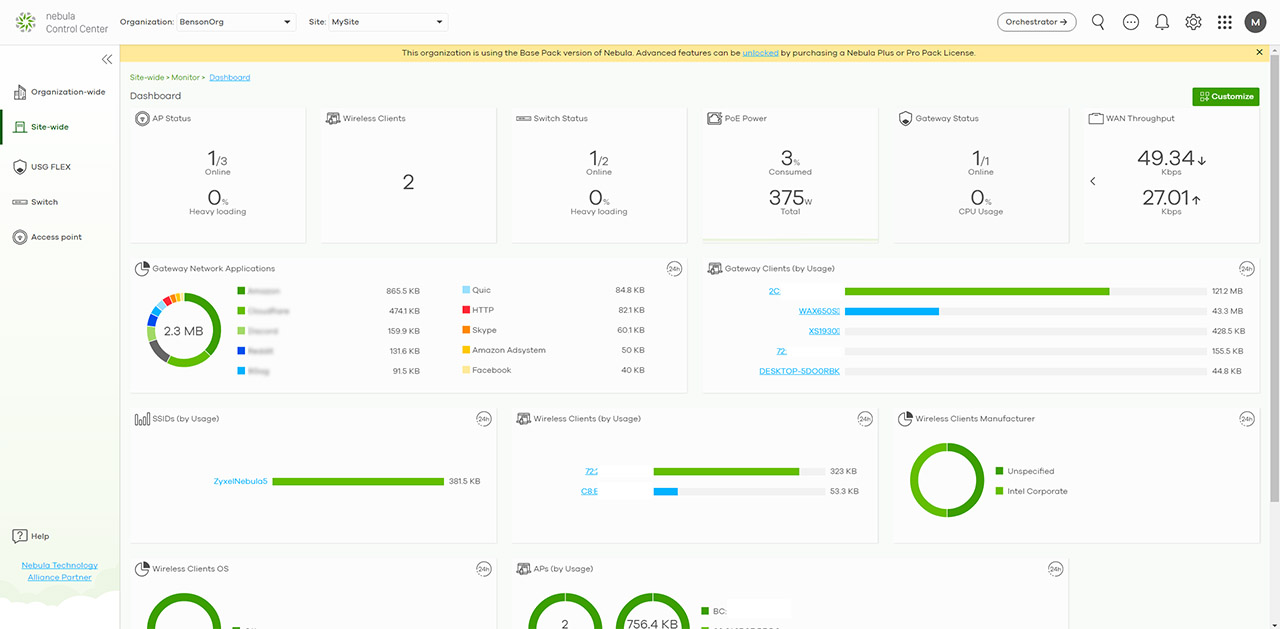
You can check out some general stats at the Site-Wide section, which will include the wireless access point (WAX650S) and the multi-Gigabit Ethernet switch (XS1930-12HP), and they all seem to work great together, but if you need the dedicated settings, then you need to check out the USG FLEX section.
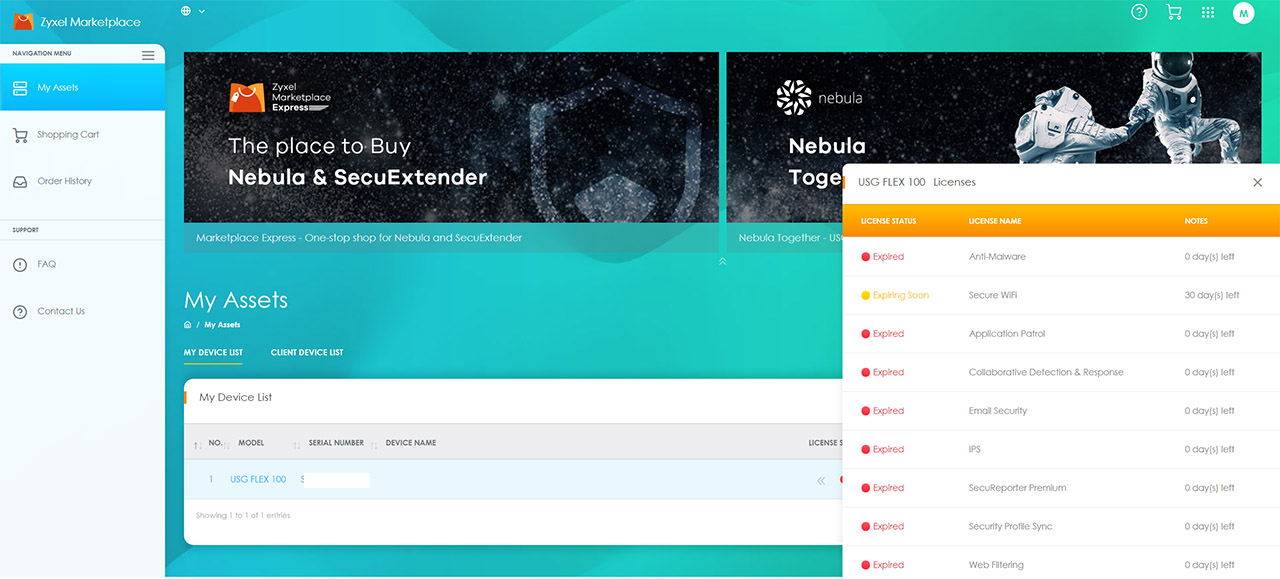
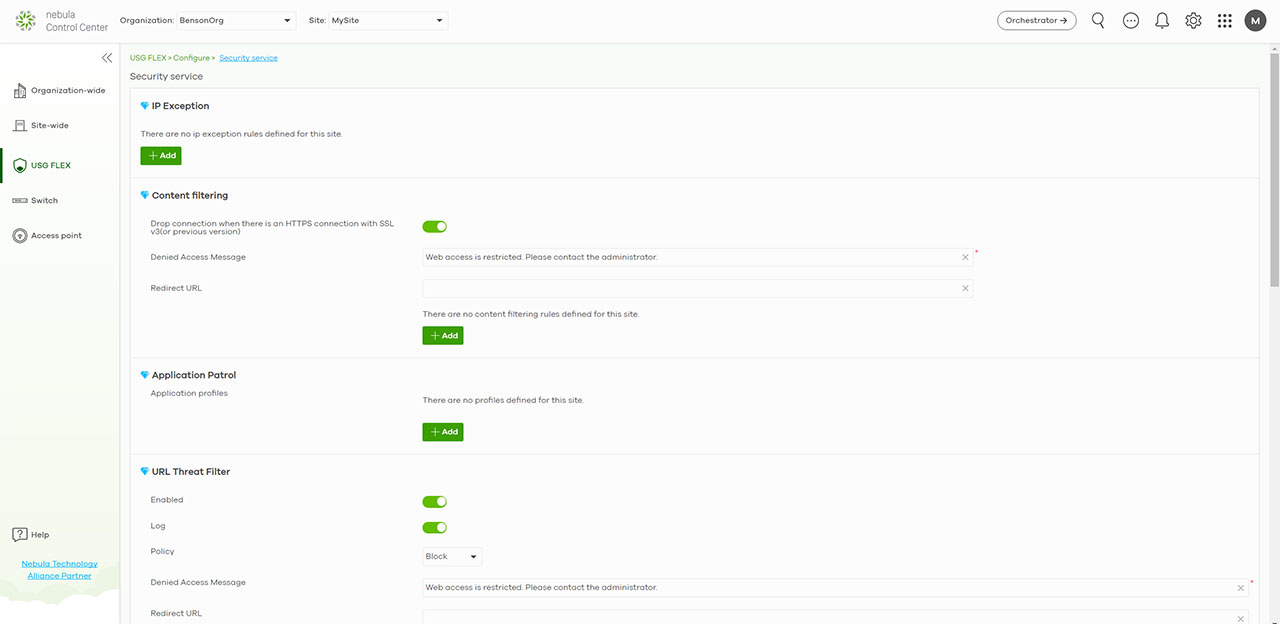
So far, Zyxel has added some general status info under Monitor, as well as all the connected clients (each with its dedicated status page) and I have also seen the SecuReporter section which takes us to a completely separate part of the Cloud and here you get to see lots and lots of status information about your network security. This includes checking the Security Indicator status (ADP, IDP, URL threat Filter, Antivirus/Malware and Mail Protection) as well as some status info about the Web activity and App Patrol. Under Configure, you can check all the security features under the Security service. This area and the SecuReporter are accessible only if you have an active license, otherwise, you can only access the Secure WiFi section ;besides the Secure WiFi, all other features had expired licenses (only in my case, obviously), so I couldn’t really explore them as part of the Cloud platform (you can read the dedicated review where the device was not connected to the Cloud).
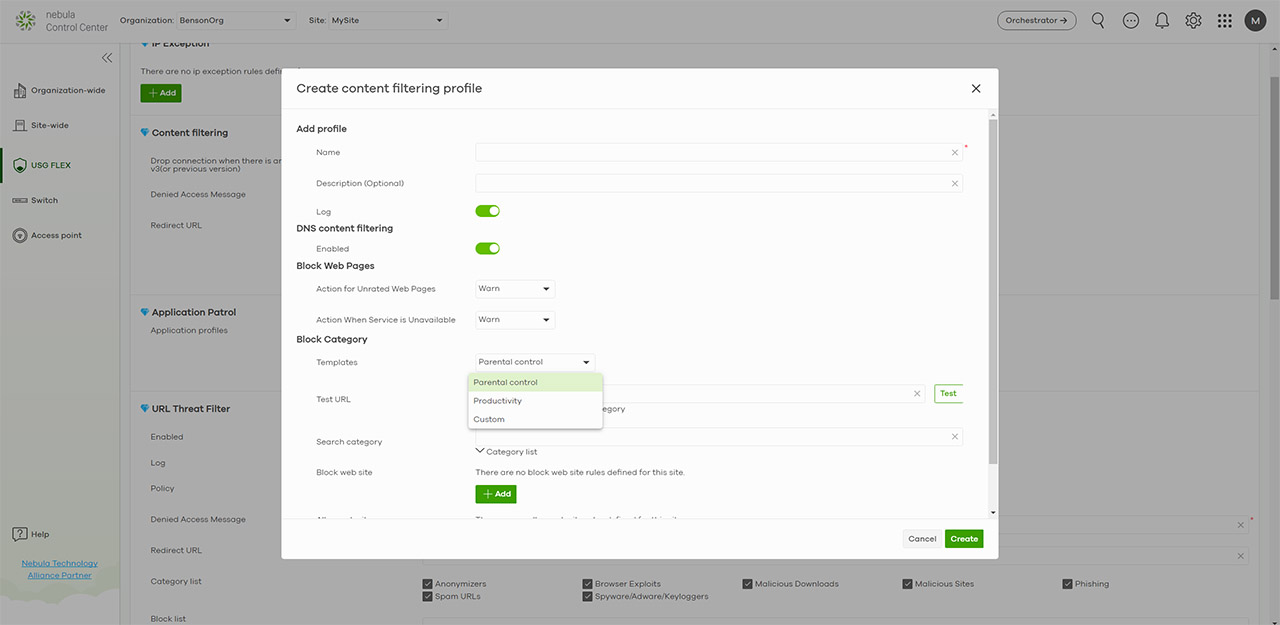
That being said, under Security service, you can create IP Exceptions which will not be filtered (white listed), followed by Content Filtering which, by default, will drop HTTPS connections with old SSL, but you can add your own profiles with filters that when triggered, can either warn you or block the webpage. Next, there’s the Application Patrol where you can define profiles for applications that will undergo the Deep Packet Inspection and I also saw the URL Threat Filter. Here, you can create a blocklist and a whitelist, you can add URLs to a specific category and set a Denied Message (there’s also an useful Log). The Anti-Malware section has two modes in which operates, Stream or Express, the latter being the faster option, since it sends a hash of the selected file type and query directly to the Zyxel Security Cloud. Lastly, there’s the possibility to enable or disable the Intrusion Detection and/or the Intrusion Prevention.
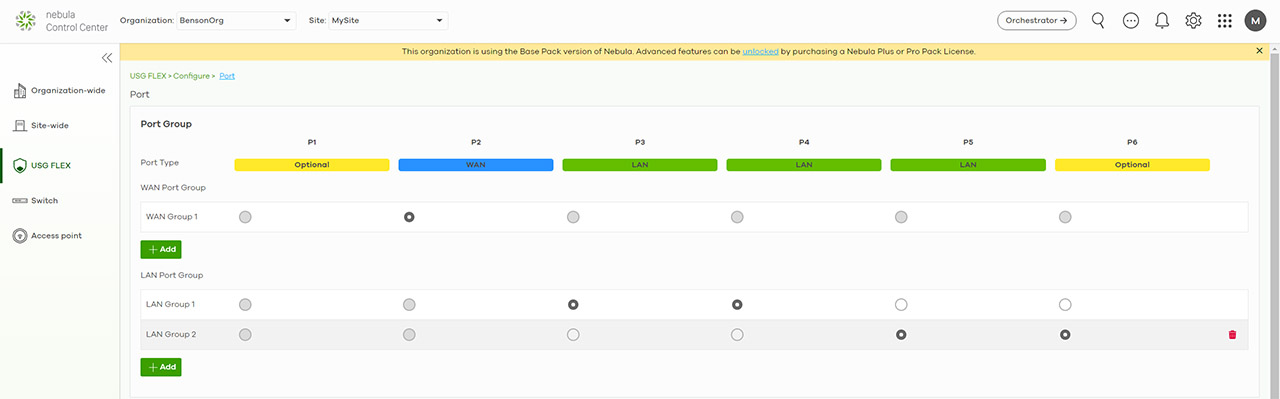
Under Configure, you get to adjust the WAN and LAN ports behavior (includes LAN Groups) and the Interface is where you can create multiple VLANs and configure the WAN Internet connection. Zyxel has also added the Policy Route / Traffic Shaping feature, the Static Route and the WAN Load Balancing could not be missing from a USG security gateway. Further down, I saw that there is also the possibility to set up NAT (Virtual Server and 1:1), Site-to-Site VPN (great for creating an IPSec tunnel between two gateways) and there’s also Remote access VPN which supports IPSec and L2TP over IPSec VPN. You can also configure the Firewall (create Security policies, Enable the Anomaly Detection and Prevention, set Session timers and create Schedule profiles for the currently used site), configure the Captive Portal for user authentication and more.
So, if you come from the web-based interface of the USG Flex 100, the integration with the Nebula Cloud Platform should be fairly painless and you do gain the possibility to configure multiple devices, including access points, switches and even other gateways a lot easier.

Mark is a graduate in Computer Science, having gathered valuable experience over the years working in IT as a programmer. Mark is also the main tech writer for MBReviews.com, covering not only his passion, the networking devices, but also other cool electronic gadgets that you may find useful for your every day life.