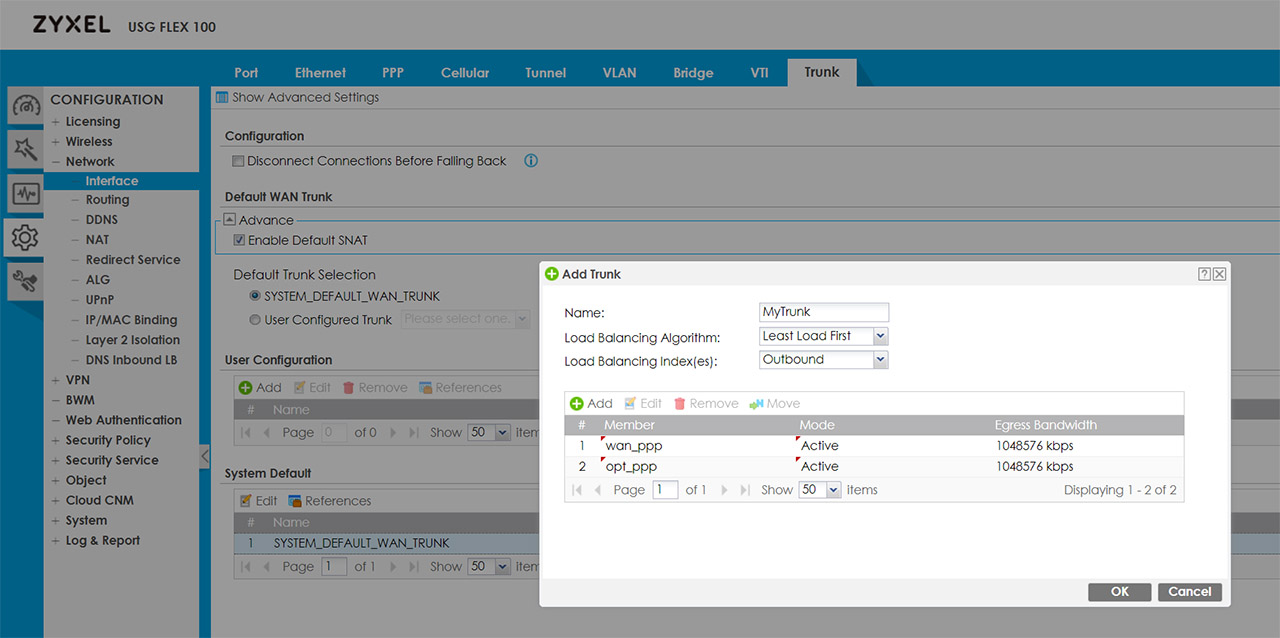
Another important aspect is that you can decide the Mode for each trunk interface, so it can either be Passive or Active and if you look towards the top of the page, you will see that under Configuration, you can enable the ‘Disconnect Connections Before Falling Back’, which means that when an Active connection regains the link, the passive ones get automatically disconnected. Besides the Least Load First, there is also the Weighted Round Robin algorithm which is best used when the bandwidth set for each WAN interface is different and the way it works is by distributing client requests to servers, each taking turns on a rotating basis. Furthermore, each interface gets assigned a weight and based on this weight, a server may handle one or more sessions.
Lastly, there’s the Spillover algorithm which sends the traffic to the first WAN interface and, when the maximum allowed load is reached, the traffic in excess is then sent to the next interface from the trunk list. If you only want to configure FailOver from the first WAN to the second and don’t want to use Trunk, you will need to go to Routing > Policy Route and set the Incoming Interface to the first WAN and the Next-Hop as the secondary and create a new Policy Route the other way around (don’t forget to Enable the Connectivity Check). I noticed that when I disconnect the Internet from the first WAN interface, it takes about 5 seconds for the second link to become active – it took about the same time the other way around.
VPN
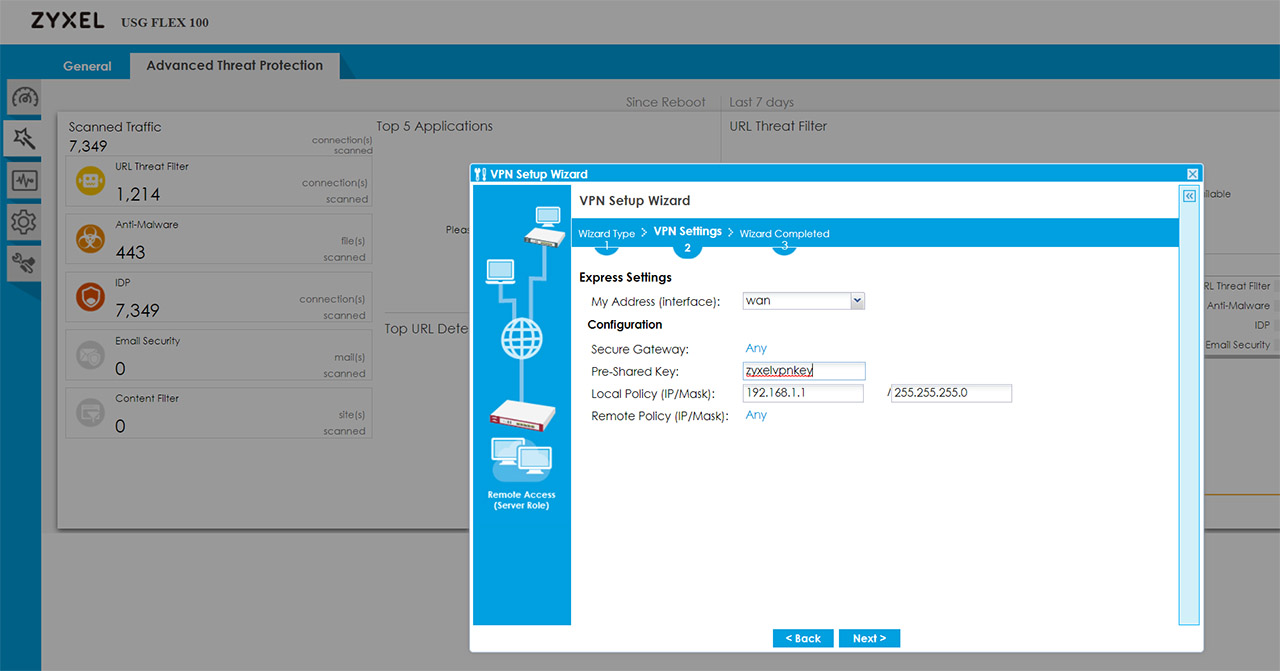
The Zyxel USG Flex 100 supports IPSec, SSL and L2TP VPN and I do like that the manufacturer has added Configuration Walkthroughs to help with setting up each one of them (quite useful with devices such as the USG firewalls, where you get to set every parameter, but it’s easy to get lost in the myriad of options). To set up the IPSec VPN, you can use the VPN Setup Wizard (the second option on the left) and follow the steps to create a new VPN Provisioning Rule; afterwards, go to Configuration > Object < Add a User and create a new IPSec VPN Client. Next, go to the Configuration > VPN > IPSec VPN > Configuration Provisioning and pair the VPN Connection to the newly create Allowed User. Afterwards, you will have to download the ZyWall IPSec VPN Client (there is a direct link from the interface – be aware that it’s license based, but you can use the trial version for 30 days) and insert the default gateway, as well as the user that you previously set up.
Zyxel has also added guides for the SSL and L2TP VPN configuration and I noticed that there is no Wizard for the SSL VPN. That being said, the process of setting up any VPNs is not really easy, but it’s made a lot more intuitive by the way the interface is designed and especially due to the dedicated walkthroughs for each type of configuration.
Security Features
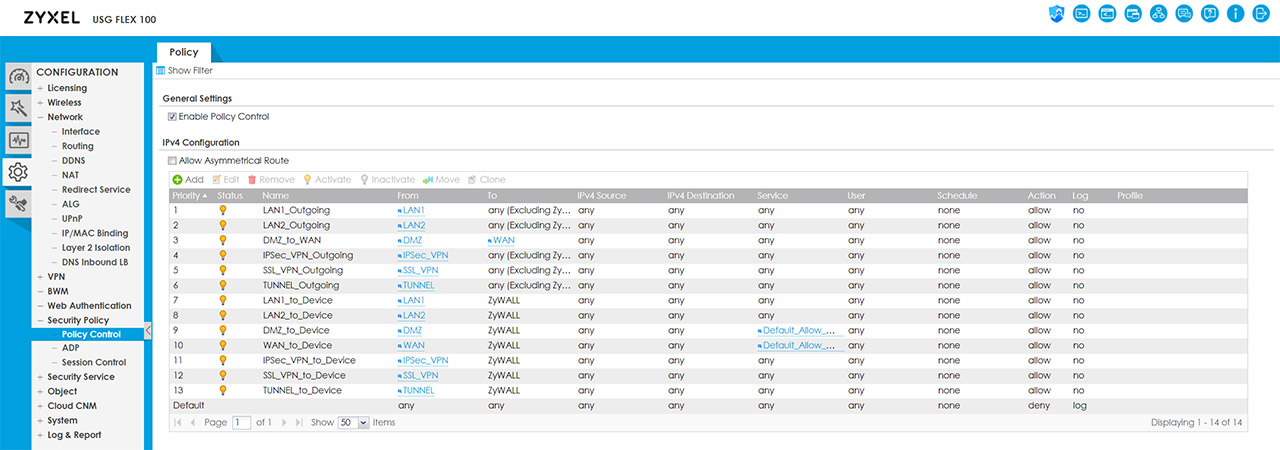
Some of the most important security features are the Stateful Packet Inspection firewall and you can check the security policies by going to Configuration > Security Policy > Policy Control; here, you can also visit the Anomaly Detection and Prevention (ADP) and add policies for the traffic source and you can also create new ADP profiles (this can be done from the Profile section and you will be able to set the Sensitivity level, the block period for the scan detection, as well as for the Flood Detection). Under the Security Service, you can create App Patrol profiles which will allow the prioritization of certain app over others, as well as the possibility to block or throttle some services based on category or name (this feature does rely on Deep Packet Inspection to get a higher degree of precision).
The Content Filter is another important feature of any Unified Threat Management appliance which allows the user to set rules for the type of content that’s allowed or should be blocked (there is a very extensive list of categories, but you can also add Custom Services) and then, there’s the Anti-Malware, where you can set which type of files to scan, the mode, create a Block/White list and more.
You can also block or allow certain types of URLs under the Reputation Filter, enable IDP (it does require a license) which is an extremely important feature for a security gateway due to its ability to detect any threats from malicious third-parties (viruses, hacking attempts and so on) but be aware that it does have an impact on the throughput, as I saw an average of 500 Mbps (from a Gigabit connection) when the IDP was enabled.
It’s also worth mentioning the Email Security (great at detecting Spam emails), the SSL Inspection (extremely useful at detecting attacks that try to get through the encrypted traffic which would otherwise bypass the normal defenses) and the IP Inspection (you can set exceptions for certain IP addresses, so they’re not affected by the Anti-Malware, UTF or IDP). Besides these security features, you can also access the SecuReporter dashboard by clicking on its dedicated link from the top right corner and doing so, will take you to the Cloud server where you can see any detected malware or blocked requests, as well as a Threat Trend (by levels of potential damage); some additional data can be seen under Analyzer (such as an ADP graph, the Top Threat Website Categories, the Blocked Applications and more).
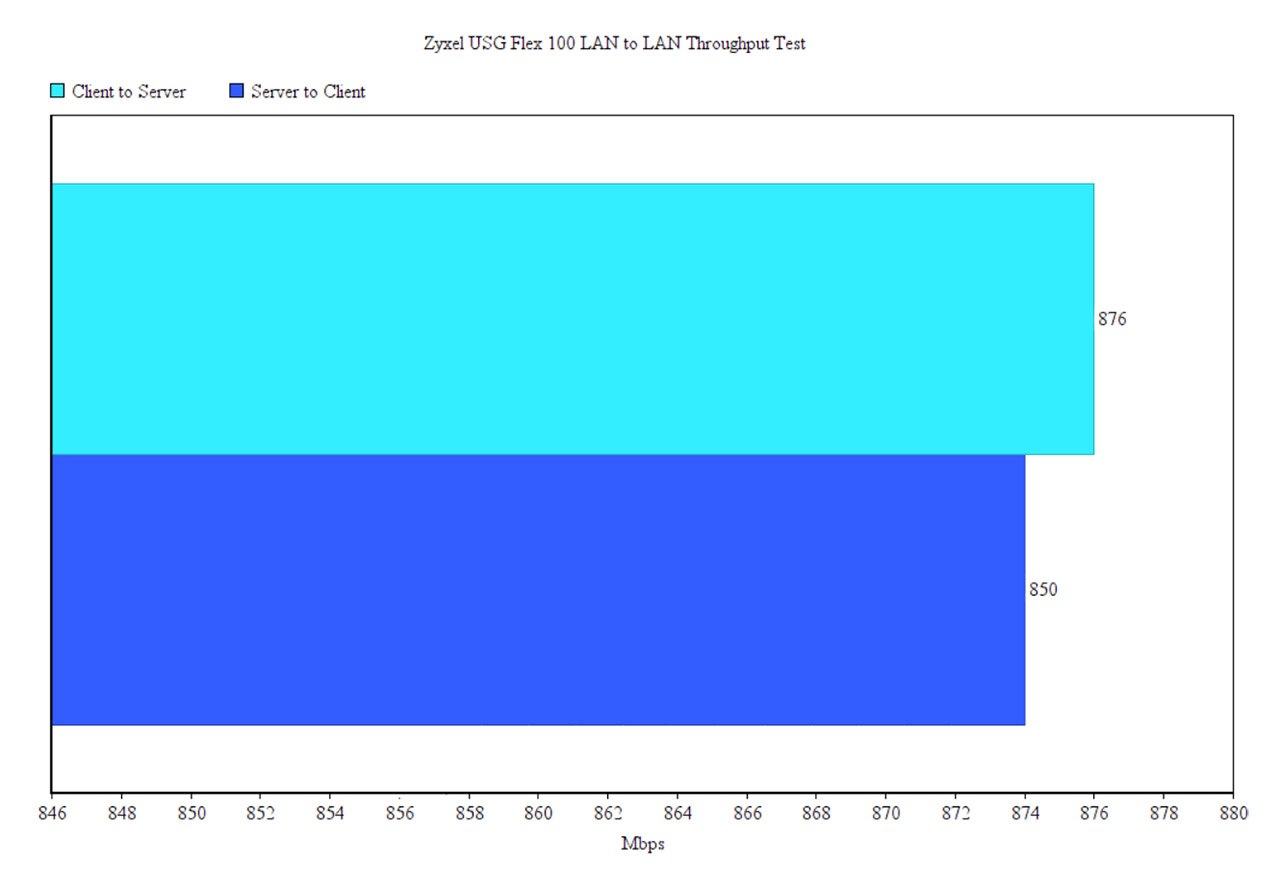
Lastly I decided to run a LAN to LAN test by connecting two computers via Ethernet cables (both devices have Windows 10 OS installed – 64-bit and both had the firewall disabled). This way, I saw an average of 876 Mbps from the client to the server and an average of 850 Mbps from the server to the client which is in line with the 900 Mbps advertised by Zyxel.
Conclusion
Considering that Zyxel has been one of the main suppliers of reliable multi-WAN security gateways for small and medium businesses for more than a decade, there are some high expectations to be met and, after running the USG Flex 100 for a few days, it does seem like the new series does tick all the boxes, especially in terms of security. You get a huge amount of control over what’s blocked and what’s allowed, there are wizards and walkthroughs to help you with any complicated configuration (including steps to set up the IPSec, SSL and L2TP VPNs) and you can balance the load between more than a single WAN port. The internal hardware has also been upgraded to handle more demanding applications without cutting too much from the throughput and the license flexibility is pretty much one of the highlighted features of this new USG series. That being said, similarly to other devices from the USG series, the Zyxel USG Flex 100 supports a huge amount of configurations and the user can adjust pretty much every aspect of their network and while that’s a plus, it can be intimidating for any newcomers. Thankfully, Zyxel has made sure that you are covered for almost any type of application that you’re trying to run, so don’t hesitate consulting the available user manuals and walkthroughs.
Zyxel USG Flex 100
-Pros
- Supports IPSec, SSL and L2TP VPN
- Anti-Malware, ISP and other security related features
- The device is very compact
- Multi-WAN support + various load balancing algorithms
- Lots of walkthroughs and tutorials available
Cons
- It does get a bit hot on the bottom side
- A lot of features (such as the IPSec VPN client) are under license

Mark is a graduate in Computer Science, having gathered valuable experience over the years working in IT as a programmer. Mark is also the main tech writer for MBReviews.com, covering not only his passion, the networking devices, but also other cool electronic gadgets that you may find useful for your every day life.