WHAT IS CUJO?
CAN A REGULAR ROUTER PROTECT YOUR IOT NETWORK?
IS CUJO REALLY PLUG AND FORGET?
WHAT OTHER OPTIONS ARE OUT THERE? (PFSENSE)
When the first smart devices came into existence and the concept of a smart home and the IoT has finally managed to materialize, a lot of people have pointed out that these new devices and the way they operate could pose a dangerous security threat for both home users and for companies if proper measures aren’t put in place.
Fast forward to present times and not much has changed in the IoT environment, people enjoy more and more to smarten up every household object (smart toasters, smart water bottles, smart mirrors and so on) and manufacturers are taking advantage of this increasing trend by quickly adding a couple of sensors, create an app and you’re set, a new device is born and everybody is happy.
Unfortunately, things are never this simple as it has been proven time and time again that a significant number of manufacturers have no idea how to implement proper security measures (or don’t have the funds, in the case of start-ups), so they will either throw a half-baked device on the market in the hopes of gaining enough budget in order to solve some of the security concerns at a later time or, in the worst case scenario, some won’t even bother with ever upgrading the firmware again.
This behaviour allowed the dangerous botnet attacks which explored already known vulnerabilities and using a large number of smart devices, managed to perform DDoS attacks against various websites (the case of the Mirai malware) and things haven’t been solved since new possible threats are coming to light every month, so new large scale attacks could be launched at every moment (such as the case of the IoT_reaper).
This has made people more aware of the risks of not having a secured network and I’ve noticed a higher demand for security-related software and hardware, which has put into the spotlight the relatively new home-suitable firewall boxes, such as Cujo, Bitdefender Box, RatTrap and Norton Core. The most popular from the bunch is Cujo, which continuously gains even more popularity with each looming threat of IoT botnets, but let’s first have a look at:
What is Cujo?
Cujo is a small device which aims at protecting your home network from outside threats, especially if you have lots of IoT devices. The small firewall box sports a very interesting design, migrating away from the conservative, industrial look and adopting a more minimalistic and modern look (but somehow ending up looking like a flower pot).
The main attraction will be the circular LEDs which will light up in different patterns in an attempt to mimic face expressions (happy eyes indicate that everything is working fine, while sad eyes indicate that the device is disconnected or offline and full eyes indicate that Cujo has detected a new threat).
But as with any other networking device, what’s on the inside is what matters the most, so let’s see what does Cujo add in terms of security as compared to a regular, but popular router (such as a standard, no frills Netgear Nighthawk R7000, as well as taking into consideration using OpenDNS for a better set of security features):
| Cujo | Regular Router | With OpenDNS | |
| • Safe Browsing (IP/DNS) | Yes | Yes | Yes |
| • Command & Control Blocking | Yes | Not by Default | Yes |
| • Antivirus and Antimalware | Yes | No | Yes |
| • Behavior Analysis | Yes | No | Yes |
| • DoS Attack Protection | Yes | Yes | Yes |
| • Local + Cloud Security Layers | Yes | No | Yes |
| • Parental Controls | Basic | Yes | Yes |
First of all, be aware that Cujo does function in a similar way as other, more difficult to set up (and often more expensive) firewall appliances (such as Pfsense boxes, Sophos or Fortigate), but it doesn’t have the same deep analysis of the content of every packet, as it just inspects the metadata of each incoming or outgoing network packet (taking into consideration the open ports, the connection protocols and more). The Safe Browsing is ensured by the IP/DNS Threat Intelligence feature which has the role of dynamically verifying if the destination IP address or DNS infrastructure matches the database consisting of any websites that are known to distribute malware, viruses, botnets or undergo phishing attacks.
At the same time, most routers will allow its users to set up the firewall rules in order to block malicious URLs, but you won’t have access to an regularly updated blacklist. If you opt to use OpenDNS (now owned by Cisco) along with your router, you will notice that it will function in a similar manner as Cujo: when a DNS request for a specific IP address has been made (while trying to access a website), a OpenDNS server will receive the request and it will verify if the website is safe or if it poses a risk to your system.
Note: Cujo underwent some updates, so now it will inspect parts of the HTTPS traffic (the unencrypted parts).
Furthermore, while most routers will protect their clients from incoming traffic, most won’t do anything against outbound traffic. That’s why it is important to understand that there are Command & Control servers which, after the malware has infected a number of devices, they will sometimes try to send commands to them, but most of the time, the communication is initiated from within a person’s infected device.
To counteract this, Cujo uses what it calls the Command & Control blocking in order to sever any attempts from the infected device to communicate with ‘its masters’. Unfortunately, by default, the Netgear Nighthawk R7000’s firewall will trust any type of outgoing traffic and, in order to protect your network, you’ll have to manually insert rules.
OpenDNS will operate in the same way as Cujo, so it will block any attempts at accessing known Command and Control Callback websites. This way, your system should remain protected against viruses and malware. Also, let’s not ignore the likes of TP-Link Deco M5 which uses Trend Micro in order to gain antivirus and antimalware protection or the newer Eero second generation which also provides anti-malware, anti-phishing, anti-ransomware and antivirus protection, but, similarly to Cujo, you’ll need to pay a monthly subscription.
Besides checking out for infected websites and blocking any inbound or outbound connection to said websites, Cujo also takes advantage of the Behaviour Analysis feature, which has the role of monitoring the traffic and detecting any type of irregularities (such as DDoS attacks) and it is a very important feature because it detects problems that were missed by the antivirus (or anti-malware) software. As expected, the Nighthawk R7000 lacks this function, but, OpenDNS does offer it under the advanced threat defenses pack.
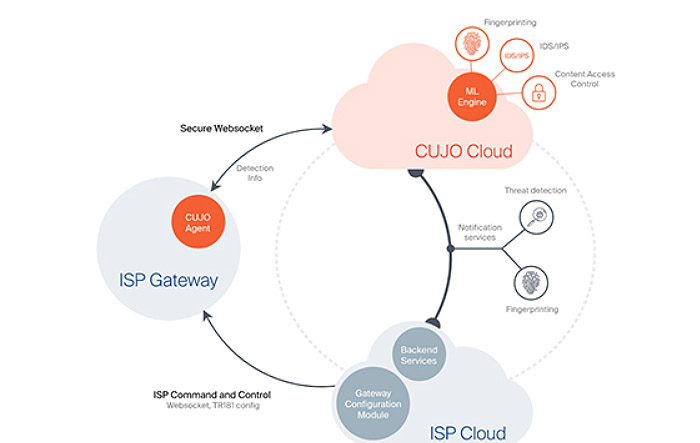
Cujo prides itself with the mix between local and cloud security layers, so the device will continuously communicate with the cloud to both create a safer environment for your devices and for building a large database in case it detects some new vulnerabilities.
The regular router won’t really use a cloud and some may even see this as a breach of user privacy, but, nevertheless, this is an increased trend even for the newest WiFi systems, which take advantage of a cloud connection to send data, so the manufacturer will find new ways to improve the user’s network (but, you don’t really have a way of tracking which data is being collected).
The Netgear R7000 falls into the first category, which means that it should not communicate with the manufacturer for improving security (but, it does seem to collect diagnostic data, so make sure to turn that feature off, since it doesn’t seem to directly improve the user experience in any way). Similarly to Cujo, OpenDNS will continuously communicate with a large number of servers for delivering enterprise-type security.
Can a regular router protect your network (including IoT devices) from hacker attacks?
Now that we saw what are the main differences between a regular router and Cujo, some people may wonder if the router firewall won’t be enough to stop any potential intrusion. If you’re having a desktop computer and a smartphone connected to a router, chances are that you are fully protected against most types of attacks (if, by any chance, the attacker bypasses the router’s security, the computer will have its own Firewall defence, so you are protected).
The smartphone security has been a delicate subject over the years, especially in the Android vs iOS debate, with the latter being regarded as the more secure mobile OS, but, similarly to Android, it still remains vulnerable to malware. At the same time, even if your phone is compromised, in the aforementioned scenario (computer + smartphone), you will still remain safe in most situations. The problems arises when you’re adding the newer smart devices into the equation, with most of them demanding interconnectivity and a continuous connection to the manufacturer’s servers.
And that’s when things become less safe, especially because some manufacturers completely disregard any security measures except offering a username and password protection system, which is sometimes left as default by the user (so the blame is usually shared). Furthermore, even if some vulnerabilities are being exposed, there are devices that won’t ever receive an update, so the user is left with an outdated device which can be exploited at any given time.
Your router will do a valiant job by default (as can be seen in the above table), but there are some settings that any user can configure to ensure that the network is even better protected:
• change the default username and password on every device: this is the most basic thing anyone can do, which makes the attack on a home network at least a little bit challenging;
• disable WPS: the WiFi Protected Setup has been created for an incredibly easy way of accessing the WiFi (without bothering with those long passkeys that you have to enter when accessing the wireless network), but it seems this system is incredibly vulnerable to both online and offline brute-force attacks and it is also very easy for a third-party user to just look at the label with printed info on the case of the router and gain access to the network;
• disable UPnP: yes, I know, that’s how most smart devices detect each other and communicate in order to give you that smart home feeling, but the problem is that this feature opens ports in a firewall automatically in order to allow access to a hosted server on a local machine, so, that makes it easy to exploit by a trojan and, once one device gets infected, it will try to find its way into your other devices – if UPnP is a necessity (and unfortunately it often is nowadays), you could try to isolate your more vulnerable IoT devices from the rest of your equipment which contains sensitive info by setting up separate VLANs (some routers will support it, but most won’t – while it may seem doable to segregate devices, the real challenge will be to configure the system to operate smoothly and to continuously adjust it when new vulnerabilities are discovered);
• configure separate WiFi networks for your guests: this is usually easy to set up (depending on the router) and it will ensure some basic protection for your personal data;
• disable Telnet and SSH: I know you must be familiar with the Mirai malware which was spread last year and used thousands of IoT devices to conduct DDoS attacks, but, have you heard about Brickerbot? No? Well, it’s a new malware which tries its way into unprotected consumer-type IoT devices and could potentially render the gadget completely unusable (or bricked, as the name suggests) – to protect your devices from this new malware (or future ones that tend to use the same approach), you need to disable or block Telnet and SSH communications;
• regularly update the firmware: I know that there are some manufacturers that won’t ever update the software of lower-end routers or IoT devices, but a large proportion will release fixes and updates as soon as a new vulnerability is discovered on their devices, so make sure to regularly check and update your devices.
The problem is that once your router has been infected, it is quite difficult to realise it and take measures since these programs use minimal bandwidth resources. You could perform scans using online tools (although not always reliable) and determine if you have open ports used maliciously, so you can do a complete reset of your device to kill the malware, but it means lots of manual work which most users would do anything to avoid (and, to be honest most don’t really know how to properly set up their router or smart devices, nor have the time to learn).
That’s where Cujo and the other home-suitable firewall appliances become an attractive option, since they promise to require almost no configuration from their users and all they have to do is plug in the device and let it do its job quietly, while they can continue their normal web surfing. But, I can’t help to wonder:
Is Cujo really plug and forget?
The ideal modern networking device is that which can be easily set up (preferably with a user-friendly mobile app) and, after the initial configuration is done, it can be left in a corner of the room and the user can forget about its existence.
Unfortunately, Cujo is quite far from ideal and it may even prove to be challenging for the usual user: you have to choose between three types of configuration, Standby (which means that the device is simply connected to your network and does nothing to protect it from any type of attacks), DHCP Mode or Bridge Mode.
To use Cujo in DHCP Mode, you have to disable the DHCP server on your router and make Cujo work as a gateway (there are instructions to do this manually or you could ask the technical team from Cujo to help you – be aware that the support is limited to routers that are on the manufacturer’s list of compatible devices).
The Bridge Mode (which should be used when dealing with more complex networks, with multiple access points and switches) puts Cujo in the middle of two routers: the first router gets connected to the Internet, while your devices will connect to the second router and you do have to disable the DHCP server on the second router. All of these necessary changes that have to be made on the router’s interface won’t appeal to the technical novices and, while the Cujo team will help the users to properly set up their devices, there just is no way you could call the small Cujo firewall a plug and forget device.
So, now that we have a more clear idea about what Cujo is and how to set it up, is it better than the firewall on your router? If it is set up properly, a good router with a solid firewall (configured correctly) will be able to withstand most types of attacks and will be able to protect your IoT devices in most cases. What Cujo adds is a second layer of protection and has the advantage of dynamically identify new threats by using a comprehensive list regularly updates on their servers.
But, as I’ve pointed out many times, people expect an easy to use device which requires no maintenance and won’t give up no more than 5 minutes for the initial set up process, so configuring their firewall, closing ports or creating VLANs won’t really happen for a large majority of the population. Cujo and the other home firewall appliances have promised to take that burden from the user and it has actually managed to do it up to a certain level (if the people are willing to go over the more complicated and non-user-friendly initial configuration), which means that there is definitely a wide audience who could benefit from this type of devices.
What other solutions are out there?
If you feel that your network may be vulnerable even if you took some precautions and you aren’t afraid to ‘get your hands dirty’ and try something more advanced, you could use pfSense, which is an open source software distribution that can be used as a firewall / router, covering a large array of applications by making use of some advanced features, suitable for both home use (for tech enthusiasts) and for businesses.
Among these features, there’s multi-WAN, VLAN, QoS, OpenVPN, load balancing, Stateful firewall, Traffic shaping and filtering and more, but the most interesting aspect of pfSense is the support for third-party packages, such as Snort and Suricata (two incredible applications for network security), Squid, Apache HTTP Server, pfBlockerNG and many more.
The one advantage that pfSense has over almost all other solutions is that it is free (while the equivalent firewall appliance from Cisco could cost thousands of dollars) and that it’s very flexible, which means it can be installed on a large variety of hardware: you could use an old computer, desktop or notebook (it will need two Ethernet ports, so an additional network card and an Ethernet switch is required), but, since it will consume a lot more power than your regular router, you could try going with some more compact devices that are provided by Netgate.
A Netgate appliance will work better with pfSense because all the requirements are being met and you’ll have a more stable implementation, but, as said before, you could build your own device as well.
So, how can pfSense help with the current security crisis in the IoT world? Quite a lot actually as it uses some advanced features to give the user the possibility of creating a heavily secured network:
• Snort: you will need to subscribe to SNORT rule sources (some free and some commercial) which will determine what will SNORT try to detect by analysing your traffic using protocol, signature and anomaly-based inspection methods: can be malware, DDOS attacks (as well as bad traffic and exploit kits), HTTP / FTP / SNMP exploits, check the user traffic and create blacklists (in order to avoid false positives as much as possible, you should also configure white lists and suppression lists);
• Suricata: a network threat detection engine which can detect real-time intrusions (IDS) and it features inline intrusion prevention (IPS) based on external rules (as well as Lua scripting support for detection of complex threats) in order to monitor the network traffic (and it also has offline pcap processing);
• pfBlockerNG: is an interesting package which gives the user the ability to allow or block traffic based on the country of an IP address, the Alexa rating of an website and more, so it goes well beyond the traditional router Firewall (it’s also great at blocking ads).
These are some of the main tools you can implement to protect your IoT network, but you can go even further and isolate them in a separate VLAN and throttle the new network to something which won’t be of much use in case of a DDoS attack, but will be enough for your smart devices choose (as well as choosing which ports to let open for outside communication).
The trouble with pfSense is that it requires a steep learning curve and will scare off people unfamiliar with setting up some advanced networking technique and this is why devices like Cujo will always have a broader appeal. Also, let’s be honest, the design of the Cujo is more relatable, more human, therefore more likeable by the masses, while the industrial look of a dedicated pfsense box is nowhere near Cujo’s ingenuity, but, technically, you could attach a pair of googly eyes on your desktop PC or pfSense firewall appliance and jiggle it from time to time to get a similar effect.

Mark is a graduate in Computer Science, having gathered valuable experience over the years working in IT as a programmer. Mark is also the main tech writer for MBReviews.com, covering not only his passion, the networking devices, but also other cool electronic gadgets that you may find useful for your every day life.